Thinking, “I shouldn’t end up in 23% who don’t prioritize IBM i security?”
Well, you of course wouldn’t end up there.
- Because your IBM i isn’t broken.
- Because your IBM i is operating at an optimum capacity.
- Because your IBM i interacting with the outside world effectively.
- Because your IBM i is doing all that it should be doing without amiss.
The question is, “How long will it be relevant?”
- Yes, you have done those timely patch fixes.
- Yes, your IBM i qualifies on those regulatory compliance audits.
- Yes, your IBM i team is closely monitoring the environment for discrepancies.
But, somewhere, deep down you are aware that there is a looming threat – cyberattacks, data thefts, ransomware, malware, and whatnot.
Reason – your business needs have evolved, but IBM i security stature hasn’t!
The matter of fact is – these attacks don’t have to be intentional and done by outsiders. There might be hidden discrepancies which may cause unintentional damage from the internal users also.
Prevention is always better than cure.
And today, IBM i security hinges on proactive prevention.
Thinking, “How can I attain a bulletproof IBM i environment?”
This read covers everything you need.
By the time you reach the end of this read, you’ll have uncovered –
- Top iSeries security challenges
- Possible solutions to tackle them
- Role of IBM i/AS400 support services
- How futureproofing IBM i helps you stay relevant
Without any further ado, let’s get started!
Protect Your Business with IBM i Security Solutions
IBM i Security – Top Challenges IBM i Users Must be Wary of!
IBM i security has never been a concern – owing to the robustness and reliability that IBM i systems are renowned for.
Yet, 77% IBM i users have cited cybersecurity as a top IBM i concern ~ As per 2025 IBM i Marketplace Survey by Fortra.
Does this question the integrity of the IBM i systems?
Well, no.
It’s nothing about integrity, nor about legacy.
It’s simply about the modern-day relevance of IBM i systems and IBM i security standards.
Let’s look at some of the top challenges that make iSeries security a top concern amongst IBM i users.
Over-Reliance on Traditional Security Assumptions
- Your IBM i is rock-solid.
- Your IBM I’s security features are enough.
- Your IBM i environment is responding well to security challenges.
But traditional iSeries security protocols and disaster recovery tactics are losing their appeal to modern-day cyberattacks.
The legacy isn’t dead but losing its relevance with the changing business needs.
We regularly speak to IBM i CTOs, and we are happy to see they still believe IBM i is here to stay. But 8/10 are concerned over the security aspect – owing to the drastically growing cybersecurity landscape.
They are aware that IBM i security needs an upgrade, a change – but somewhere the “Set-it-and-forget-it” belief is holding them back from acting.
AS400 security has never been a concern – thanks to the robust architecture and security practices. But, with changing business dynamics, and cloud computing in the game – your IT environment needs reconsideration.
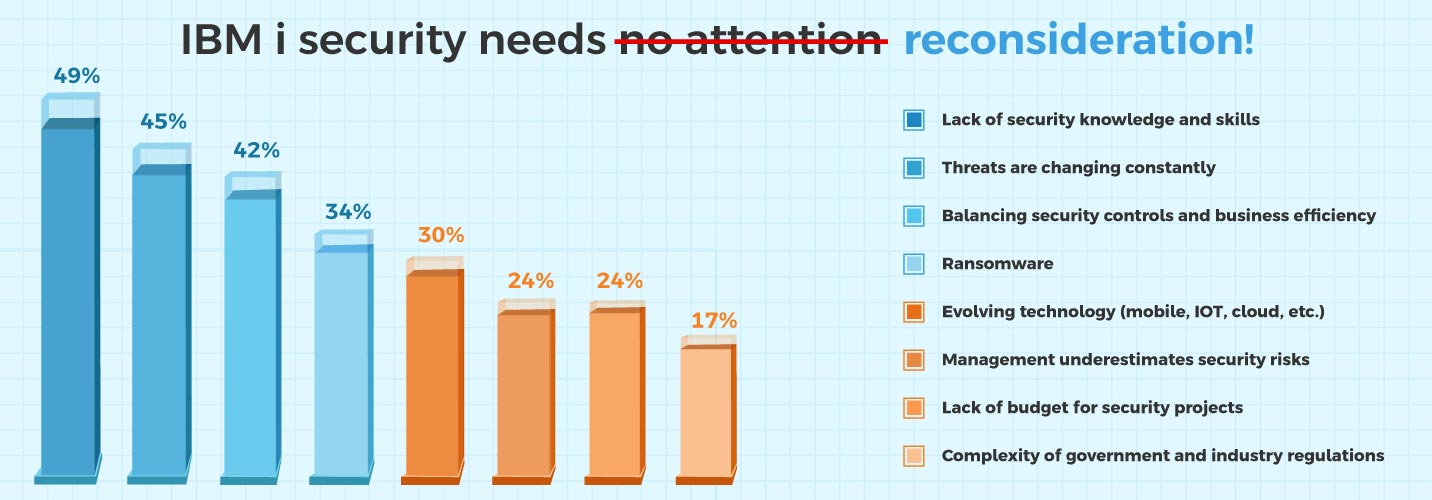
Thinking, “Why it matters?”
It matters because –
- Modern-day IBM i systems aren’t isolated – they are integrated with APIs, web-services, and third-party solutions.
- The integrations create multi-touch entry points for viruses, and malicious factors.
- The traditional user permissions and default security configurations can’t withstand modern-day ransomware & cyberattacks.
Surprisingly, only 37% of IBM i users have implemented antivirus & ransomware protection ~ As per 2025 IBM i Marketplace Survey by Fortra.
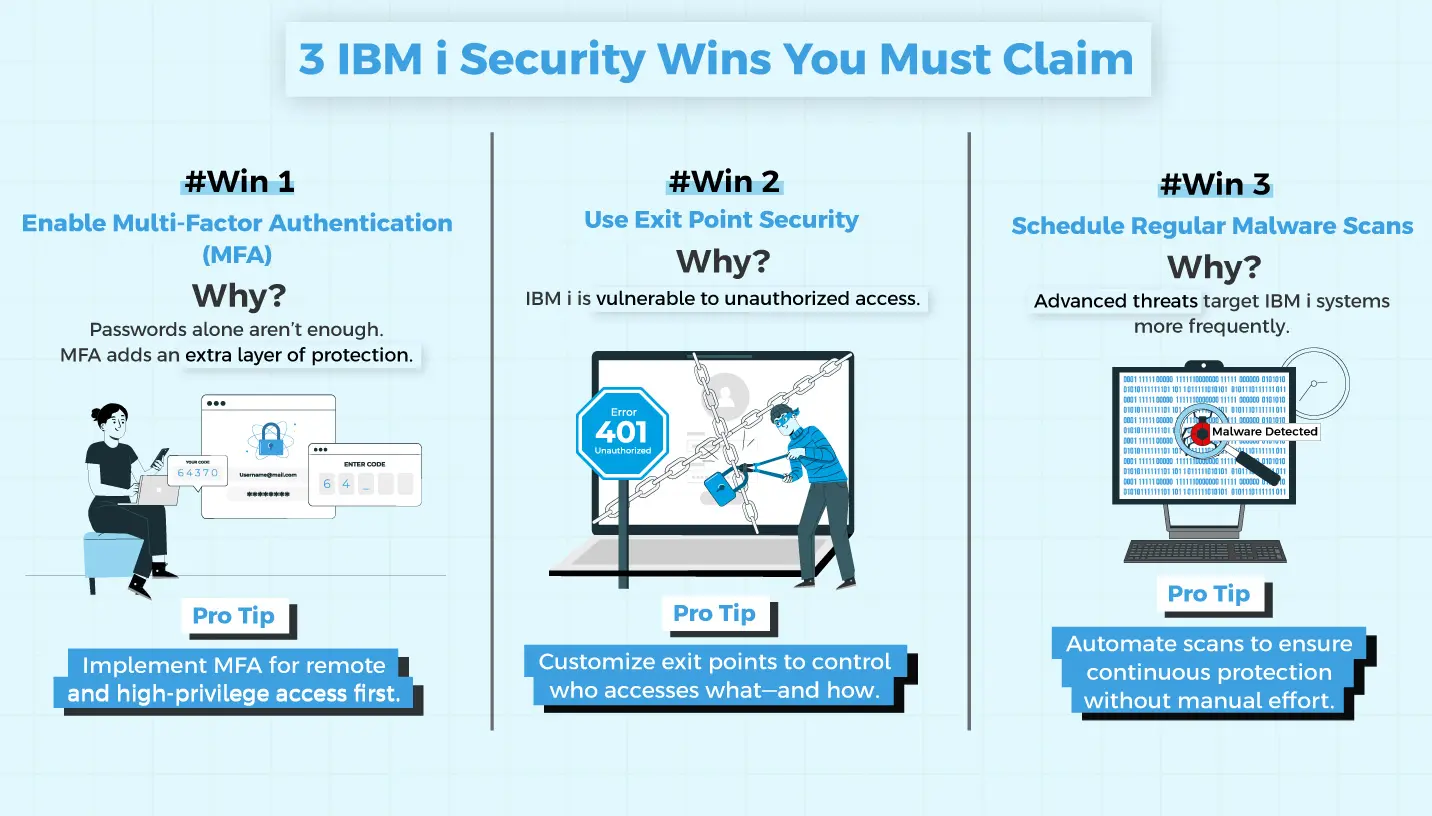
Thinking, “What can save us from this?”
Here’s what can save you –
- Have a stringent security audit routine in place
- Reduce excessive reliance on native IBM i tools, implement modern IBM i security solutions
- Prioritize exit point security monitoring, antivirus implementation for early intrusion detection
Lack of Visibility into User Access and Privileges
AS400 administration is a job of high responsibility.
Administrating who gets to see, access, and utilize what resources is tough.
Your team have prioritized and monitored user access and privileges diligently – there’s no doubt about it.
But the lack of visibility creates ambiguity as far as IBM i security is concerned.
Over the period, rather let’s say decades – your AS400 administrators have changed. What often goes unnoticed is – the user profiles they created, the roles, and access permission they assigned.
They might have walked out of the door for you – but the user profiles, and access permissions they created might still be in the system.
And this lack of visibility on unaccounted user profiles and access permissions lead to system vulnerabilities.
Thinking, “Why it’s a worrisome concern?”
It is because –
- It may invite an unintentional insider mistake
- Unnoticed user profiles & access permission are the biggest threats for data theft
- It creates opportunities to bypass IBM i security controls and execute commands without being flagged
About 49% of organizations cite a lack of security knowledge and skills as a barrier. It’s not just about tools—it’s the lack of awareness of your team to recognize these blind spots ~ As per 2025 IBM i Marketplace Survey by Fortra.
Thinking, “How can this be avoided?”
Here’s what you must do –
- Scrutinize user profiles and permission using IBM i security solutions, regularly
- Deploy role-based access control to restrict user permissions to resources
- Leverage auditing tools to record logs for the sensitive resources shared among your IBM i users
Underutilization of Exit Point Security
Do you know why IBM i security wasn’t a big concern back then in time?
Why IBM i users were not concerned about iSeries security provisions and security practices?
It’s because – IBM i applications that handled critical business transactions, operated in isolation.
Today, in the modern-day business world, where we want to integrate IBM i applications with modern-day solutions and third-party applications – IBM i security has become a leading concern.
More integrations, more entry points for cyber attackers and ransomware threats.
In technical terms – IBM i applications communicating with the outside world means more exit points to secure.
Thinking, “Why securing exit points is so important?”
It is because –
- Unsecured exit points double the risk of data leak – from both internal employees & external attackers
- Your IBM i environment might get exposed to unauthorized access
- Un-seized exit points invite critical risks including malware infiltration to data exfiltration
Surprisingly, only 43% of IBM i led organizations actively prioritize exit point security. This results in an unidentified gap between the perceived & actual security stature of the IBM i environment ~ As per 2025 IBM i Marketplace Survey by Fortra.
Thinking, “How can this be tackled?”
Here’s how you can tackle this –
- Implement IBM i security solutions to monitor exit points, regularly
- Establish stringent access policies based on IP addresses, user profiles, and time-of-day
- Monitor the IBM i application logs & alerts for unusual activities
Limited Security Integration with SIEM and Centralized Monitoring Tools
Investing in a SIEM (Security Information and Event Mangement) system is a superior counter major for IBM i security that you have in place.
Early detection of security incidents helps you execute your disaster recovery plans effectively.
But there’s a small disconnect that’s often neglected – SIEM systems operate in silos, in isolation from your IBM i environment.
This disconnect leads to difficulties. Your security teams don’t get enough time to respond to security incidents. They don’t have real-time visibility into the events and hence they struggle to investigate the root causes, post the breach.
Thinking, “How this affects the overall IBM i security stature?”
Here’s how –
- Lack of visibility into event logs, user activity, and access control violation brings your security provisions to a standstill
- Your mission-critical data and IBM i applications can be compromised, and you can only plan to recover but not prevent
As your business evolves, regulatory compliance needs evolve too! This disconnects between your IBM i environment & SIEM systems may invite critical questions from industry mandates like PCI DSS, HIPP, and GDPR.
Thinking, “How can this be avoided?”
Here’s how you avoid it –
- Prioritize integration of your IBM i system logs with SIEM systems and IBM i security solutions
- Monitor system alerts and suspicious activities like login failure, unauthorized access in real time
- Leverage AS400 security managed services to rectify and eliminate integration challenges
Skills Shortage and Outdated Security Practices
Your IBM i has been powering mission-critical operations for decades now.
And, we know your thankless to those hands that contributed in building up those mission-critical workflows, tirelessly managed AS400 workloads, and maintained your IBM i environment in its top shape – your IBM i workforce.
As technology ages, so do the personnels.
The sad part – your tech can be modernized to stay relevant, but the workforce has to be retired at some point in time.
It’s a harsh truth to face – but your seasoned IBM i workforce must walk out of the door, one day.
As you prioritize IBM i security, your IBM i workforce has a crucial role to play in building, maintaining, and modernizing the security procedures.
Thinking, “How much does IBM i skill shortage affect IBM i security?”
The damage is real, here’s how –
- Lack of skilled IBM i professionals invites misconfigurations, delays in patch fixes, and defers the responses to evolving threats
- You’ll continue with traditional iSeries security provisions without paying much heed to modern-day IBM i security solutions, and automations
With over 45% of survey respondents citing the “evolving threat landscape” as a top concern, you can’t afford a reactive approach. Future-proofing your IBM i security should be your priority ~ As per 2025 IBM i Marketplace Survey by Fortra.
Thinking, “What can be done to upkeep my IBM i security”
Here’s how you can do that –
- Rope in IBM i security experts or consulting help to be on the top of IBM i security updates
- Leverage IBM i security managed services to extend your in-house teams and expertise
- Focus on upskilling for in-house teams to keep the relevant with the modern-day IBM i security needs & solutions
Next, let’s understand how we’ve helped our customers achieve IBM i environments that are bulletproof against modern-day security threats.
Strengthening IBM i Security – The Integrative Systems Way
Amidst the evolving cybersecurity landscape, firewalls, and antiviruses aren’t enough to seize the risk.
If you ask us, as an IBM Silver Business Partner – we encourage proactive IBM i security measures as a norm.
We believe early detection creates opportunities to prevent and eliminate damage, without disrupting the operations.
The goal is to futureproof your IBM i against IBM i security risks, without affecting your core operations.
Our seasoned team of iSeries security experts stays current with the IBM i security trends and strategically deploys customized IBM i security solutions to fortify the overall security stature of your IBM i environment.
We don’t want you to believe us, but what we have done for our customers over the last two decades.
Let’s understand how we helped our customers strengthen their IBM i security posture, with some real time use cases.
AS400 Consulting – Identify and Eliminate Security Gaps
A US-based Manufacturing Company was struggling with unprecedented system slowdowns, untraced data access logs, with a user authorization model that hadn’t seen an upgrade for years.
Problem
There was a knowledge gap for IBM i security practices among the in-house team of AS400 professionals. The regulatory compliance audits were difficult to pass.
Solution
Our seasoned team of IBM i security consultants assessed their IBM i environment – analyzed user profiles, exit points, and security provisions in place.
We devised a stringent IBM i security strategy to help them navigate the risks involved. We helped seize the exit points, deployed role-based access control, and brought an alignment to industry compliance standards.
Result –
As a result, they attained –
- 75% reduced unauthorized access attempts
- Aligned compliance reporting for the annual audits
- Improved confidence in the overall IBM i security stature
- Comprehensive documentation on the security architecture – delivered within 6 weeks
Bottom line – Integrative Systems AS400 consulting services aren’t focused on sheer advice – it’s more about practical implementation of iSeries security practices to ensure our customers attain a secure IBM i environment.
Need to improve your IBM i security controls?
We’re here to help you implement the right solutions.
AS400 Support & Maintenance – Secure Day-to-Day Operations
A US-based Logistics Company was operating its warehouse chores on IBM i and experiencing close to no visibility into system vulnerabilities. The patch fixes made were inconsistent, and the backup verification process was not in place.
Problem
Their internal team of IBM i professionals was burdened looking after every other IBM i challenge, neglecting potential security blind spots.
Solution
They signed for AS400 Support & Maintenance services.
Our team of IBM i security experts analyzed their IBM i environment for patch fixes made, weak links, and OS version upgrades.
We helped set up a proactive monitoring schedule for security reviews based on factors like role-based access, user profiles, incident response handling, object-level authority.
Our iSeries security experts help deploy an alert system to report anomalies in time.
Result –
As a result, they were able to attain –
- 90% availability with reduced downtime with preventive maintenance
- Thorough back-validation, with automated audit trails
- 365 x 24 x 7 system monitoring for uncertainty & violations
- Relieved burden of serious security risks from the internal team, to help them focus on strategic tasks
Bottom line – Integrative Systems AS400 support & maintenance services aren’t focused on sheer maintenance activities – it’s more about helping our customers attain a secure IBM i environment with high uptime.
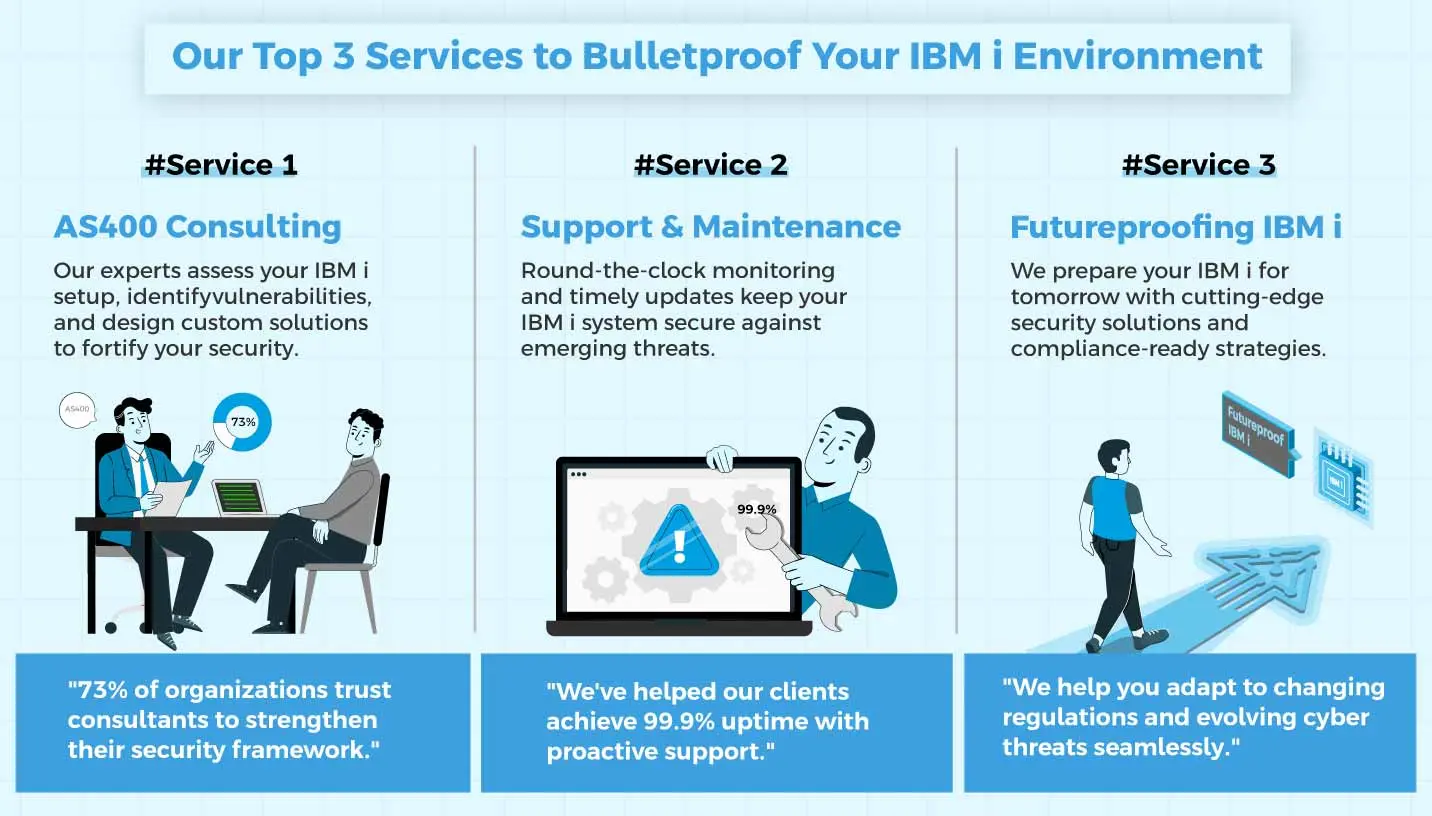
Futureproofing IBM i – Security That Evolves with Your Business
A US-based Retail Chain that existed on multiple locations was struggling to move their IBM i workloads to cloud with a hybrid strategy.
Problem
Their IBM i security software wasn’t compatible with modern-day integrations. The APIs were exposed to security vulnerabilities, user provisioning processes were struggling, and automation didn’t exist.
Solution
With Integrative Systems Futureproofing IBM i services, our team of AS400 experts revamped their IBM i security module for compatibility with the new hybrid cloud environment.
We helped them integrate SIEM systems with the new hybrid cloud infrastructure for holistic monitoring & prevention of security incidents.
We also optimized their IBM i workloads for the new environment & automated patch rollouts.
Result –
As a result, they were able achieve –
- Secure movement from on-premises to hybrid cloud environments without compromising data safety
- Secured web services fortified with next-gen authentication
- Real-time integration of SIEM system and IBM i applications with automated security alerts
- 45% improvement in deployment timeline for new workloads with automation
Need to improve your IBM i security controls?
We’re here to help you implement the right solutions.
Bottom line – Futureproofing your IBM i refers to reviving your IBM i environment to make it more flexible, scalable, and stringent following the best IBM i security practices.
The goal is to ensure your IBM i environment and IBM i security standards evolve with modern-day business needs.
Integrative Systems – IBM i Security Services Provider of Your Choice
We realize IBM i security isn’t just another priority – it’s a differentiator when we talk about the relevance of IBM i to modern–day business needs.
At Integrative Systems, our team of IBM i security experts bring you the balanced mix of strategic foresight and effortless execution.
Whether you are seeking support with IBM i skills, a safety net to fall back on for AS400 support or a partner to trust with futureproofing your IBM i applications – we got you covered!
Drop us a line at contact@integrativesystems.com and our IBM i security experts will reach out to you within two business days.
Let’s mark your IBM i safe from the modern-day security threats, today and for the days to come.
Need to improve your IBM i security controls?
We’re here to help you implement the right solutions.
IBM i Security – Frequently Asked Questions
1. What is IBM i security?
Ans- IBM i security means security standards defined to mark IBM i systems, environments, and assets safe from any sort of unauthorized access, data theft, and cyberattacks.
2. What are common AS400 security vulnerabilities?
Ans- Inadequate user authentication, extensive user privileges, lack of data encryption, outdated system configurations, and ineffective auditing practices- these are some of the common AS400 security vulnerabilities.
3. What solutions are available for AS400 application security?
Ans- Role-based access control, end-to-end data encryption, and regular system log monitoring are some of the common IBM i security solutions that you can implement for AS400 application security.
4. Why are AS400 security managed services important?
Ans- IBM i security managed services help you upgrade your IBM i security posture. A team of AS400 experts help implement the best IBM i security practices, offers actionable insights on security, and ensures your IBM i environment is compliant. The key advantage of investing in managed services is your internal team is freed to focus on strategic initiatives.
5. How can IBM i security experts assist in strengthening system security?
Ans- IBM i security experts keep up with IBM i security best practices. They analyze your IBM i environment for discrepancies, spot weak links, and implement security best practices to keep your IBM i systems relevant in the modern-day business landscape.
Need to improve your IBM i security controls?
We’re here to help you implement the right solutions.